An open access journal
An open access journal
RDDT-MS: Real-Time Decryption and Detection of Malicious Traffic Using Man-in-the-Middle Proxy and SnortML
Abstract
In network system construction, the issue of network traffic security is of paramount importance. Against the backdrop of strengthening national cybersecurity, traffic inspection plays a significant role in continuously enhancing the security capabilities of network systems. However, as more and more traffic is transmitted using the HTTP protocol over SSL/TLS encryption, this not only provides protection for legitimate communications but also facilitates covert attacks by malicious actors. Traditional traffic detection systems (such as Snort and Suricata) struggle with the challenge of inspecting encrypted traffic, and their detection rules are typically configured based on known attack patterns, making them less effective against evolving new types of attacks.
To address the aforementioned issues, this paper innovatively proposes a comprehensive traffic detection frame. The main contributions of this work are summarized in three parts:
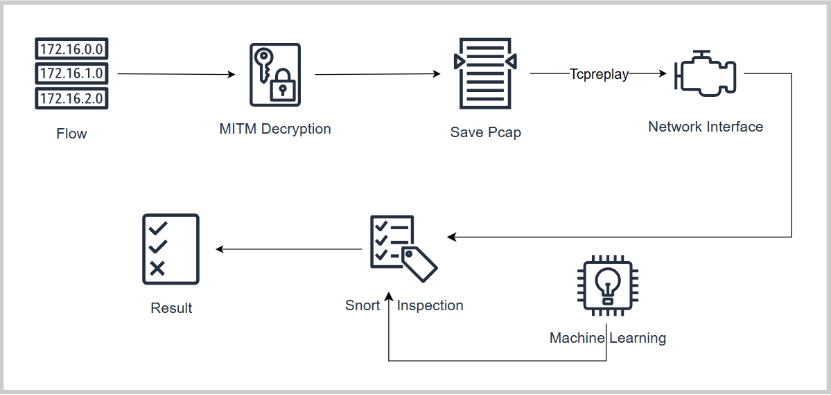
1.Real-time Traffic Decryption and Detection Framework: We have designed and implemented an efficient real-time traffic decryption and detection architecture that cleverly integrates man-in-the-middle proxy technology to enable real-time decryption of HTTPS encrypted traffic.
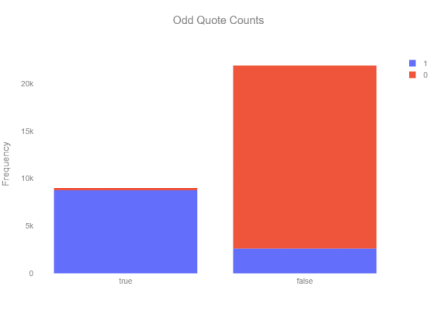
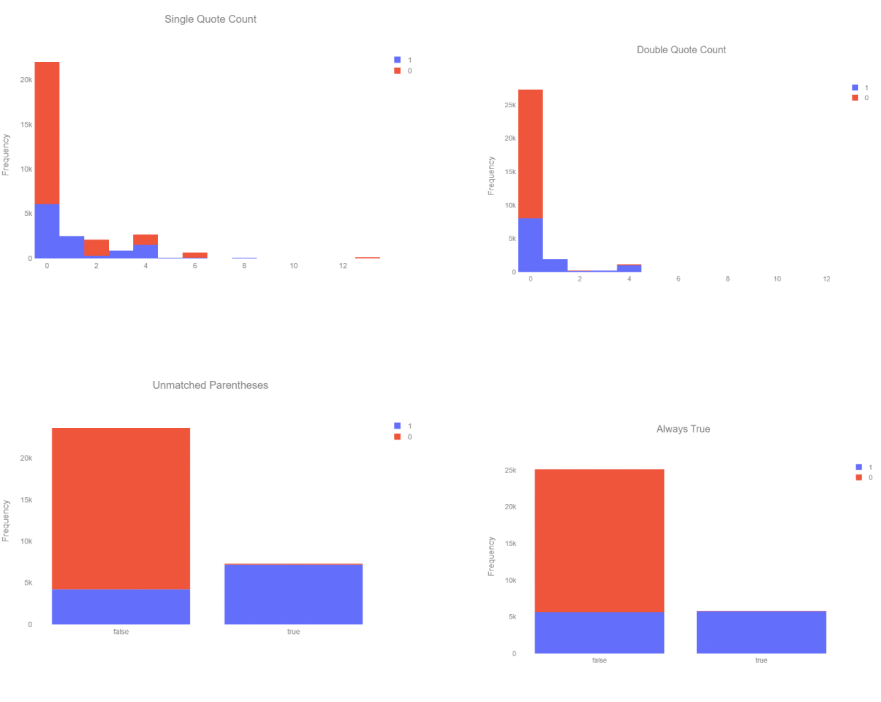
2. Model Training and Validation Using an SQL Injection Dataset: To validate the effectiveness of the framework, we utilized a dataset containing SQL injection attacks to train the detection model and applied it within the framework to evaluate its capability to detect unknown attack traffic.
3. For the development and testing of the SnortML plugin: To enable real-time traffic feature extraction in SnortML, we added feature extraction capabilities to the SnortML detector and used the tcpreplay tool to simulate complex network traffic scenarios.
Through our research, we have achieved automatic detection and efficient defense against real-time, encrypted, and potentially unknown attack traffic. Experimental result clearly demonstrate that the framework has significantly improved the accuracy of encrypted traffic detection, providing strong technical support and innovative ideas for building a safer and more robust network environment.
Show Figures
Share and Cite
Article Metrics
References
- Xinhua net. The network security and information leading group held the first meeting [EB/OL]. http://www.cac.gov.cn/2014-02/28/c_126205866.htm.2014-02-28.
- H2C. Cybersecurity Vulnerability Situation Report 2023.2024. https://www.h3c.com/cn/d_202402/2056604_30003_0.htm
- Jia Afang, Chen Shi, Wu Shuang, et al. Encryption Trojan Detection Method based on HTTPS Covert tunnel [J]. Journal of Information Engineering University, 2019, 4.
- Xie J, Li S, Yun X, et al. Hstf-model: An http-based trojan detection model via the hierarchical spatio-temporal features of traffics[J]. Computers & Security, 2020, 96: 101923.
- Anderson J P. Computer security threat monitoring and surveillance[J]. Technical Report, James P. Anderson Company, 1980.
- Zalbina M R, Stiawan D. HTTP Attack Detection System Based on HTTP Inspect Preprocessor and Rule Options[J]. Available on academia. edu, last accessed April, 2023, 10.
- Leng Feng, Zhang Cuiling, Chen Wanyu, et al. Analysis of attacks from Protocol Information of Snort rules [J]. Computer Applications, 2022.
- Mallik A. Man-in-the-middle-attack: Understanding in simple words[J]. Cyberspace: Jurnal Pendidikan Teknologi Informasi, 2019, 2(2): 109-134.
- Gibert D, Mateu C, Planes J. The rise of machine learning for detection and classification of malware: Research developments, trends and challenges[J]. Journal of Network and Computer Applications, 2020, 153: 102526.
- Snort. Talos launching new machine learning-based exploit detection engine. 2024.03.15. https://blog.snort.org/2024/03/talos-launching-new-machine-learning.html
- Halfond W G J, Viegas J, Orso A. A Classification of SQL Injection Attacks and Countermeasures[C]//ISSSE. 2006.
- Kaggle. biggest-sql-injection-dataset. https://www.kaggle.com/datasets/gambleryu/biggest-sql-injection-dataset/data